What is an IT risk?
When researching for a common definition of IT risk, there is a lot to consider. To simplify the discussion, let us break this down into the following components.
IT: Information technology, the business unit responsible for deploying and managing applications, databases, operating systems, and infrastructure used by employees, customers, vendors, and other stakeholders of the enterprise every day. No matter where you work, most, if not all, business processes leverage technology in some way, shape, or form.
Risk: The International Organization for Standardization (ISO) defines risk as “effect of uncertainty on objectives”. A principal objective of the IT function is to provide technology services and solutions for how our organizations collect and maintain information used for decision making. Therefore, in an IT context, risk can generally be grouped using the acronym CIA – confidentiality, integrity, and availability – to describe the likelihood and impact a particular IT risk has on this core objective. As internal auditors, we would expect to see management design and implement internal controls over IT risk. Common IT controls include passwords (confidentiality), program change (integrity), and data replication (availability).
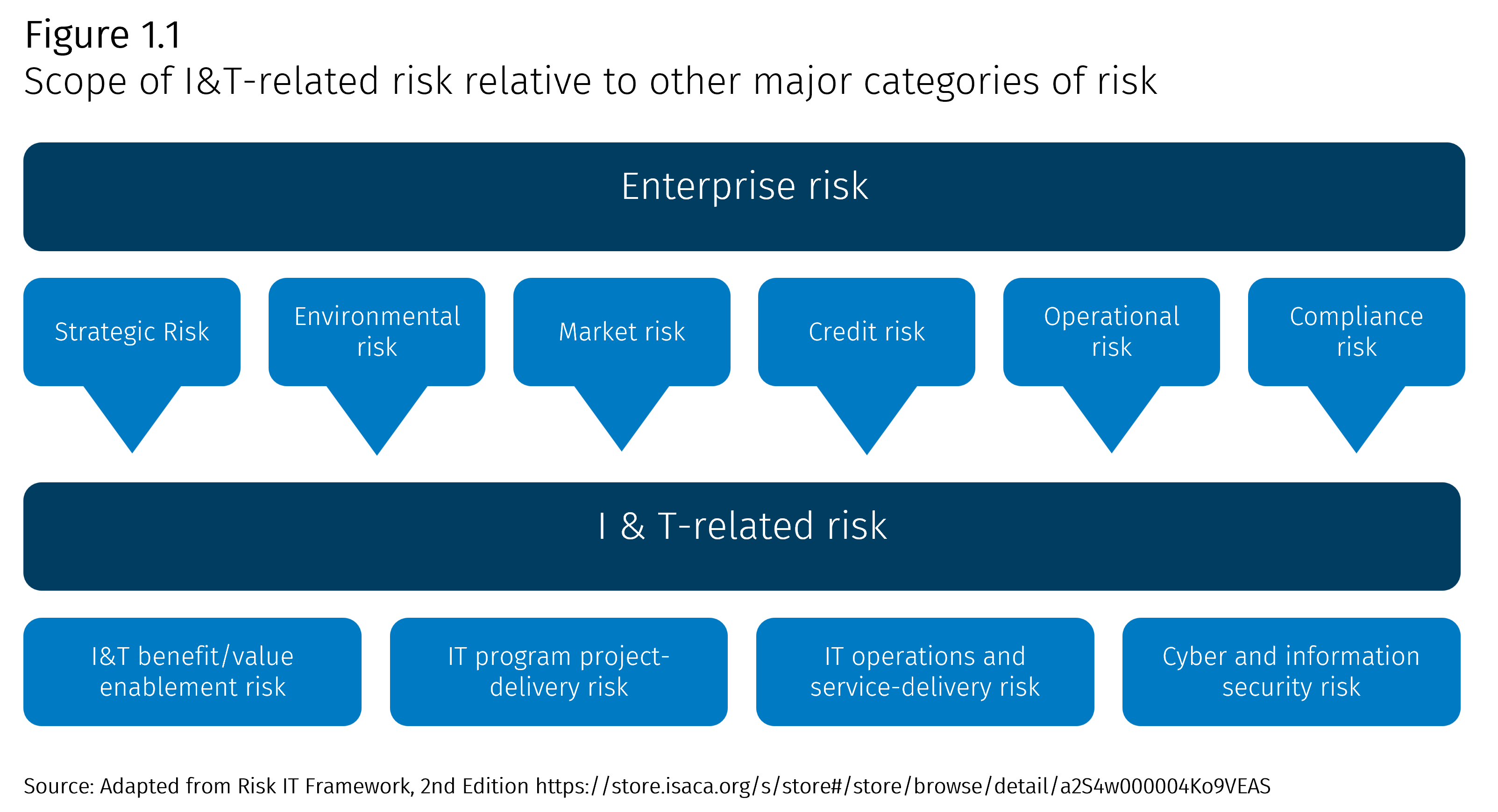
Now that we have defined what IT risk is, the diagram below will help to further simplify the overall types of IT risk. It comes from the ISACA’s Risk IT Framework, 2nd Edition. The bottom row identifies how IT risk is grouped across four buckets. The diagram also clarifies how IT risk is embedded within common enterprise-level risk pillars and the wide-ranging impact IT business processes typically have on organizational objectives. In my opinion, this is a reminder that IT risk management plays a vital role in overall risk management and that technology remains a fundamental component of running an organization.
What are examples of IT risk?
Let’s continue by breaking down the four IT risk buckets shown in the ISACA figure above. It’s important to remember that with IT risk, the risk statement can be “big picture” or very granular. By no means is the following an exhaustive list, but I will provide examples for each of the four categories and challenge you to review a few of your own risk and control matrices to see what you can come up with.
- IT benefit/value enablement risk: If the proposed technology solution does not deliver value, the organization could lose money on the investment. I often see this type of IT risk aligned with the software development lifecycle business process, usually before the solution is developed or purchased. Common IT risk could include a lack of due diligence performed on a software vendor, or if a solution is developed internally, not clearly addressing the core business problem the solution is supposed to solve.
- IT program project-delivery risk: Technology solutions are often complicated and time intensive investments, and if not delivered effectively, could cause time and financial overages. Similar to IT Benefit/Value Enablement Risk, I often see IT Program Project-Delivery Risk aligned with the software development lifecycle business process. Common IT risk could include a lack of governance over the development or implementation of IT assets.
- IT operations and service-delivery risk: As a former IT auditor, I spent many years evaluating “what could go wrong” with IT business processes such as logical access, program change, and computer operations. Common IT risk here includes unauthorized access to technology resources, inadequate governance of changes made to existing systems, and information not being backed up in case of an outage.
- Cyber and information security risk: ISACA embeds Cybersecurity and Information Security under the Information Technology umbrella. According to ISACA’s “Getting Started with Risk Management” white paper, “cybersecurity is related to IT, because technology is often the vector through which cyber risk is realized”. Several more granular issues, such as security breaches, data loss or corruption, and malware, fit into this bucket. The cyber and information security risk space is often the headline generator, where if something goes wrong for an organization, more likely than not, it’s because of a breakdown in this space.
Take another look at the above graphic and see what other risks you can derive from this analysis. What patterns do you see? Do the patterns fall more into known, formally documented risks, or more emerging risks, such as AI?


